SSI: The Identity Layer for Decentralization
Trustless environments do not rely on a-priori trust relationships or authorities as the source of truth. Notably, participants involved into a trustless ecosystem collaborate to define the source of truth. Their interactions naturally rely on trust relationships, agreed upon identity of individuals or organizations.
Among the emerging identity models, we consider the Self-Sovereign Identity (SSI) [1] as an especially promising model that allows a subject to build and prove its identity in a decentralized manner. The SSI model leverages Decentralized IDentifiers (DIDs), Verifiable Credentials (VCs) and Verifiable Presentations (VPs) as the core technologies. The SSI model allows digital identities to autonomously create and update their own identifier. Each DID is resolved to the associated DID document, which contains public information of a self-sovereign identity (e.g. public keys controlled by the subject). DID documents are published on distributed ledgers, guaranteeing at the same time autonomy to DID controllers and authenticity and integrity to DID resolvers. Subject’s claims are managed in accordance with the “Triangle of Trust” [1] model. A trusted Issuer asserts something about the subject in a VC. Then, the subject sends a VP that includes the issued VC to the credential Verifier. Finally, the Verifier evaluates whether the subject satisfies the policy relying on claims provided by a trusted Issuer. SSI provides an identity layer that is as expressive as a physical credential and verifiable through cryptography. Moreover, credential Holders maintain full control over both the data they share and on their own identifiers.
The SSI model involves peer-to-peer interactions, but it can also be used in the client-server architecture that is typical of the Web. In this scenario, we consider the SSI as a promising decentralised alternative for implementing client authentication at the application layer. The client establishes a secure communication channel with the server using the Transport Layer Security (TLS) protocol [2] with server authentication only. Assuming the client already has its self-sovereign identity, it then creates a VC, signs it and sends it to the server for authentication. Following successful authentication, the server will also verify the client’s VC claim(s) for authorisation before granting access to the requested service/resource.
Transition to Post-Quantum Cryptography
The SSI model is currently based on traditional cryptography, but it can benefit from the cryptographic agility included in its design to adapt and respond the looming threat posed by Cryptographically Relevant Quantum Computers (CRQCs) [3]. This growing threat is already prompting governments and industry to adopt solutions based on Post-Quantum Cryptography (PQC). Motivated by this emerging need, the QUBIP project [4] has taken a practical step towards the transition of the SSI ecosystem to PQC by designing and implementing Quantum-Secure:
- Plaintext Credentials with Post-Quantum/Traditional (PQ/T) hybrid and solely Post-Quantum (PQ) approaches,
- Anonymous Credentials with selective disclosure capabilities.
Quantum-Secure Plaintext Credentials
The transition to PQC of Plaintext Credentials means switching from traditional to PQ or PQ/T hybrid key pair generation, signature generation, and verification. In the SSI ecosystem, this implies to select and adopt appropriate PQ signature algorithms to be used by the Issuer and Holder to sign the VC and VP respectively, and by the Verifier to verify these signatures for authentication purposes. After a comprehensive performance assessment and a critical comparison, we have selected the Module-Lattice-based Digital Signature Algorithm (ML-DSA) [5] as the primary option for this transition, then we have implemented it in practice on the IOTA Identity library [6], an open source SSI project maintained by the IOTA Foundation. The library allows DID documents, VCs and VPs to be created through simplified management of its primitives, according to the W3C specifications. The work consisted of adding the ML-DSA family algorithms and developing the necessary functionality for Issuers, Holders and Verifiers to sign and verify signatures using the chosen PQ algorithms. The hybrid approach, on the other hand, required more changes due to the combined management of two keys, one Traditional (Ed25519) and one PQ (ML-DSA 44/65), in the creation, management and verification of signatures. The work proudly carried out by our research group has been finally reviewed and merged into the library and it is now available to the whole SSI open-source community [7].
Moreover, to bring the post-quantum transition work to a level of usability compatible with real end‑user adoption, we have also integrated the new cryptographic capabilities of IOTA Identity framework into a platform able to reflect how these promising technologies could be used in real-world applications. For this reason, we have developed a novel browser wallet extension (currently only available for research purposes) that enables users to create their own quantum-secure identity directly at the application level.
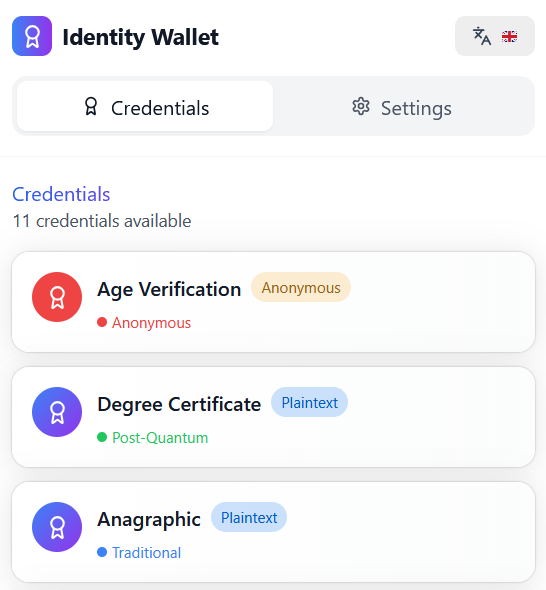
Note that plaintext credentials based on traditional cryptography represent a mature technology, widely adopted in different contexts and suitable to a transition to PQC. Nonetheless, credential systems based on plaintext credentials do not protect the privacy of the Holder because the VC with the claim(s) and the signature of the Issuer are exchanged in plaintext. In this sense, plaintext VCs result in linkability and traceability of Holders. For this reason, our wallet also supports the creation of Anonymous Credentials, implemented through the traditional BBS signatures [8] [9]. These credentials allow for the selective disclosure mechanisms, a privacy-preserving alternative that enables the Holder to manage its VC by choosing the level of information to disclose for authentication purposes.
Quantum-Secure Anonymous Credentials
Anonymous credentials play a key role in the SSI ecosystem by enabling privacy-preserving selective disclosure of specific attributes in the credential [10]. Unlike plaintext credentials, they allow Holders to prove certified statements, such as compliance with an age requirement, without revealing unnecessary attributes that can result in linkability across multiple presentations. These properties are particularly relevant in decentralized and trustless ecosystems, where users must retain control over both their identity data and its disclosure.
From a post-quantum perspective, many anonymous credential schemes currently deployed or under standardization rely on cryptographic assumptions that are not considered quantum-resistant, including pairing-based constructions such as BBS [8] [9]. This limitation has motivated a growing body of research on lattice-based alternatives, which are widely regarded as a promising foundation for post-quantum anonymous credentials.
As explained in the previous QUBIP blog post by Carlo Sanna [11], anonymous credentials are typically realized through a Proofs of Knowledge of a Signature (PoKS), combining digital signatures with efficient zero-knowledge techniques to support selective disclosure within the Triangle of Trust.
At the beginning of the QUBIP project, we analysed the state of the art to identify a suitable PQ anonymous credentials scheme. We noticed that just few promising solutions and frameworks were available in the scientific literature, all based on lattice assumptions, such as those proposed by Libert et al. [12] (with a proof size of at least 670 MB, thus impractical), Jeudy et al. [13] (~640 kB), Lai et al. [14] (~500 kB), and the framework defined by Bootle, Lyubashevsky, Nguyen, and Sorniotti (BLNS) [15]. Among them, we selected the latter because the BLNS framework presented in [15] can provide a compact credential, small proof size (~125 kB), and strong security properties (i.e., unlinkability, even against colluding Issuer/Verifier, and non-malleability preventing fake attribute proofs) [11]. Moreover, the BLNS framework was the candidate showing the highest maturity for a potential software implementation, with a detailed pseudocode already available in [15] and with security properties appropriate and relevant to the Web scenario considered by the QUBIP project.
After this initial selection, we adapted the BLNS framework [15] to the SSI operating principles and data models, we implemented it in C++ language, and we performed an initial experimental assessment. We have described such new software implementation in a conference paper that we have presented at 2nd Workshop on Quantum-Secure Networks and Systems (QSNS25) and is also available on Zenodo [10].
In addition, we published our implementation in open-source [16] for the benefit of the whole SSI community, and we look forward to receiving feedback and suggestions for improving the performance and the security of our implementation. Note that in the design of the data structures and functions, we prioritized the readability of the code, its portability and the flexibility on security parameters with respect to the pure performance. In this sense, we avoided relying on specific CPU instruction sets and/or parallelization/multi-threading. These implementation choices had the objective to ease future maintenance and possible improvements on the algorithms and to ensure a good flexibility on the parameters for achieving higher security levels. In [10] we have presented some promising performance for a 128 bit security level, even if the code still has significant room for optimization.
To the best of our knowledge, apart from our open-source code [16], only another implementation of the anonymous credential scheme in [15] is publicly available: the LaZer library [17]. Note that our code [16] is a direct implementation of the BLNS framework, maintaining as much as possible the notation for functions and variables used in the original paper [15]. On the other hand, LaZer [17] has a different purpose and ambition: it is designed as an extensive library for lattice-based zero-knowledge and succinct proofs, suitable to ease the implementation of different quantum-safe schemes and protocols (e.g., blind signatures, anonymous credentials, aggregate signatures, etc.). In fact, LaZer implements the BLNS framework just as a python demo script (i.e., anon_cred.py) among multiple schemes and protocols that are provided as use cases of the library. Another key difference of our implementation [16] with respect to LaZer is that we intentionally limited the number of dependencies, basically requiring just two external libraries (i.e., NTL and GMP) that provide a generic arithmetic backend to support basic mathematical operations on lattices. The implementation may also leverage FALCON reference implementation [18] as an optional component that can be enabled to speed up some specific operations done by the Issuer (i.e., key generation and Gaussian sampling algorithms).
Conclusions and Future Work
In this blogpost we have presented our contribution to the PQC transition of the SSI ecosystem, consisting in the design and implementation of Quantum-Secure Plaintext Credentials and Anonymous Credentials. Among the SSI assets developed within the QUBIP project, we have presented our contribution to the IOTA Identity framework [6] and our novel browser wallet extension for managing quantum-secure credentials. Moreover, we have introduced our open-source implementation of the BLNS framework [16], a novel PQ anonymous credentials scheme that already demonstrates promising performance at a 128 bit security level. However, there is still significant room for optimization [10]. In this sense, we are currently working to further improve the efficiency of some specific functions in the code. Apart from possible changes inspired by [17] and [19], our future work will continue to investigate and assess other recent theoretical and implementation results beyond the state of the art to keep pushing the limits and improving our code. In detail, we plan to do a comparative evaluation of some alternative anonymous credential and emerging blind signature schemes proposed in the recent publications. Moreover, we also intend to present our implementation and results to relevant standardisation tables which, at the time of writing, are still focusing on the pre-quantum BBS solution [8] [9]. In conclusion, we strongly believe that our novel SSI assets that we have developed, the lessons learned during the PQC transition exercise in the context of QUBIP [4], and our proactive dissemination of the achieved results will positively impact and will shape the future evolution of the SSI ecosystem, for a secure, trustless, and decentralized identity management.


