Integrating PQ HW SE into embedded devices
Alberto Battistello, Maria Chiara Molteni (Security Pattern)
29/09/2025
Introduction
The advent of quantum computing poses a significant threat to the security of classical cryptographic systems. To address this, the QUBIP project is pioneering the integration of Post-Quantum Cryptography (PQC) into resource-constrained embedded devices. This effort focuses on creating a robust hardware and software architecture to future-proof Internet of Things (IoT) devices against emerging quantum threats. This post details the integration of a Post-Quantum (PQ) hardware Secure Element (SE) with an STM32 microcontroller, leveraging an enhanced version of the Mbed-TLS library to establish a quantum-resistant communication channel.
Mbed-TLS Enhancements for PQ/T Hybrid Communication
A significant part of this work involved enhancing the Mbed-TLS protocol stack to support Post-Quantum/Traditional (PQ/T) hybrid communication, aligning with emerging standards designed to secure systems against both classical and quantum adversaries.
The enhancement comprises a dual-layer upgrade to the key exchange and digital signature mechanisms.
- Key Exchange: A hybrid scheme combining the classical x25519 (Elliptic Curve Diffie-Hellman) with the PQC algorithm ML-KEM-768 (Kyber) has been implemented, as proposed in [1]. This ensures that compromising one algorithm does not compromise the security of the session key.
- Digital Signatures: To authenticate communication, the system integrates hybrid signatures using Ed25519 with ML-DSA-44 or ML-DSA-65. Each message is signed with both a classical and a quantum-resistant algorithm; successful verification requires the validity of both signatures, providing a layered defense model.
Furthermore, the implementation supports PQ/T hybrid certificate chains extending to the Root of Trust (RoT). The chain utilizes ML-DSA algorithms, striking a practical balance between robust security and the computational efficiency required for constrained environments.
The result of this work is the pq-mbedtls repository of the QUBIP project, that contains a custom PQ version of Mbed-TLS which leverages hardware implementations of the SE and is available here: https://github.com/QUBIP/pq-mbedtls.
MCU Architecture
The demonstration platform integrates a standard microcontroller with a powerful FPGA acting as a Secure Element.
The primary MCU is a Nucleo-144 STM32F4 development board, chosen for its strong computational performance, energy efficiency, and wide adoption in the IoT sector. The Secure Element is implemented on a Kintex-7 FPGA, which provides sufficient resources (478K LUTs) to execute all necessary cryptographic algorithms efficiently.
Communication between the MCU and the SE is established over an I2C bus. This channel is secured using the Secure Channel Protocol 03 (SCP-03). To further harden the system against quantum attacks like Grover’s search algorithm, work is underway to implement the enhanced S16 version of the protocol, which increases the security level from 8 to 16 bytes (S8 to S16 [2]).
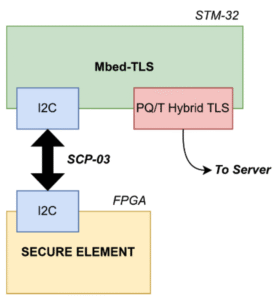
Figure 1: Architecture of the MCU-based IoT device implementation.
A key feature of this architecture is its flexibility. The platform can be configured to perform cryptographic operations entirely in software on the MCU or to offload them to the dedicated hardware within the SE via alternate function mapping. This offloading capability is critical for achieving high security in resource-constrained devices.
The result of this work is the pq-mqtt-client-mbedtls repository of the QUBIP project, that contains the software artifact to run a PQ/T hybrid MQTT client-subscriber node on the Nucleo-144 STM32F. It uses a custom PQ version of Mbed-TLS which leverages hardware implementations of the SE and is available here: https://github.com/QUBIP/pq-mqtt-client-mbedtls.
Conclusions
One of the objectives of the QUBIP project is demonstrating a complete hardware and software solution for integrating a hardware-based, post-quantum Secure Element into a typical embedded IoT device. By enhancing Mbed-TLS with hybrid cryptographic schemes and designing a flexible MCU-SE architecture, this work provides a practical and robust blueprint for building next-generation devices that are secure by design against both current and future quantum threats.


