PQC Implementation on IoT: Challenges and Solutions
Eros Camacho Ruiz (CSIC)
08/01/2024
Introduction
The Internet of Things (IoT) paradigm has grown up rapidly in recent years and it is supported by functional and heterogeneous infrastructures that are not prepared to face the future quantum attacks. Defined by a network of embedded devices equipped with sensors, processing units, and internet connectivity, IoT offers unparalleled opportunities for enhancing efficiency and convenience of modern digital societies [MRT15]. Nevertheless, the convergence of IoT and hardware security presents distinct challenges: on the one hand, strong measures to protect sensitive information are needed; whereas on the other hand, some applications impose strict constraints, needing low power usage and compact form factors.
To transition towards Post-Quantum Cryptography (PQC) in IoT, it is essential to study the performance of PQC implementations on current embedded systems. This analysis on several platforms will reveal the directions to concentrate efforts. The majority of these endeavours focus on hardware (HW) implementation of the components that demand higher computational resources. Some preliminary key points are identified in the design of PQ HW implementations, including acceleration of most-time demanded operations, reduction of power consumption, minimization of resources (i.e. memory, chip size area), miniaturization of systems to ease the development of portable solutions, and resilience against side channel and fault injection attacks with the inclusion of countermeasures.
The Secure Element to ease the transition to PQC
A Secure Element (SE), integrating HW functions into a single design, provides a solution to ease the transition of IoT to PQC. A Secure element is a critical component in ensuring the security of interconnected systems in the IoT frame, whereas it is designed to withstand attacks and protect sensitive data.
As it is illustrated in Figure 1, SE encompasses several cryptography functions such as:
- PQC Encapsulation and Decapsulation: the methods for securely sharing a secret among two or more devices to prevent unauthorized access.
- Key Derivation: the generation of one or more keys from a secret value.
- Key Storage: a secure repository for storing cryptography keys.
- Key Generation: the required algorithms to generate pairs (private and public) of keys used in the context of PQC.
- MAC: the generation of authentication codes for message verifications.
Moreover, other HW crypto functions can be implemented such as HW accelerators for performance purposes and/or hash functions. In essence, the SE plays a pivotal role in the transition of IoT to PQC while enhancing the speed and security of critical cryptographic primitives, contributing also to the overall performance and efficiency of the IoT systems.
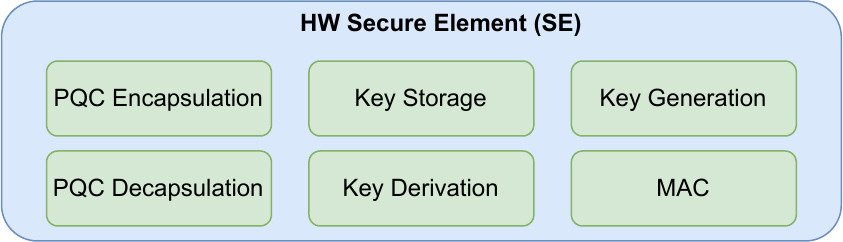
Figure 1: Illustration of the Secure Element.
IoT designs
The QUBIP project addresses two IoT designs with the PQC secure element to gain knowledge on PQC HW implementation and consequently on the transition to PQC of IoT, while showing the enhancement in terms of security. The two design flavours are illustrated in Figure 2. Essentially, the primary distinction between these two proposals relies on the level of constraints of each device. The first type is designed for highly constrained IoT devices, while the second type is focused on more powerful devices.
The first flavour is based on a microcontroller unit (MCU) that operates a simple Real-Time Operating System (RTOS). Due to the limited resources available, the SE is implemented in a separate chip from the main MCU.
The second flavour is based on a microprocessor unit (MPU) that runs a Linux distribution designed for embedded systems. In this case, the SE is implemented on the programmable part of a System on Chip (SoC), which also embeds the main processor running Linux. In this more powerful case, the hardware primitives can be re-designed in parallel architectures to achieve a high performance.
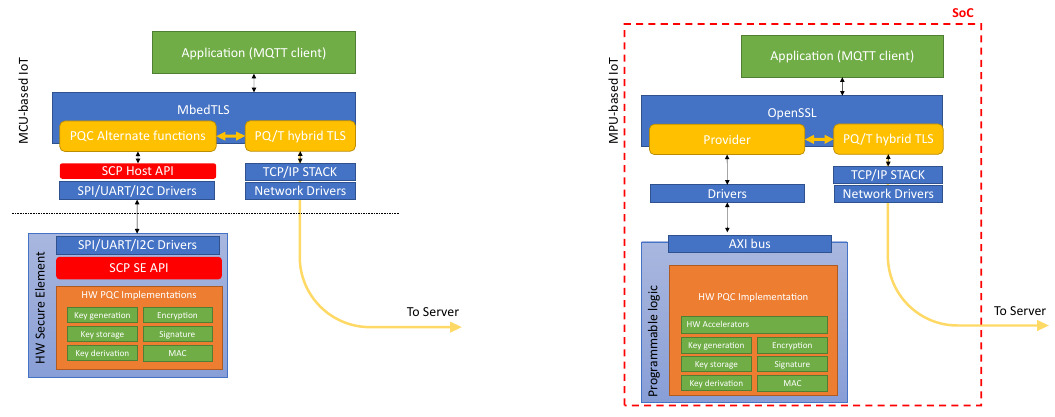
Figure 2: Proposed designs for the IoT devices: (left) constrained MCU-based IoT device, (right) MPU-based IoT device.
Starting point and next steps
With the goal of addressing the transition to PQC, CSIC-IMSE have already performed some tests involving IoT platforms. The first (short video at this link) involves two IoT devices (a Raspberry Pi 4B [RPi23] and a Pynq-Z2 [PYN22]) establishing a shared secret using CRYSTALS-Kyber [ABD+21]. The test has proved the feasibility of the implementation and serves as a foundation for the development of HW accelerators for a set of PQC algorithms, including but not limited to CRYSTALS-Kyber [ABD+21] and CRYSTALS-Dilithium [DKL+21]. Note that by leveraging the findings of [CRMRSSB23], it is possible to strike a balance between security and resource utilisation in the IoT context, thus improving the performance of the algorithm.
References
| [ABD+21] | Roberto Maria Avanzi, Joppe W. Bos, Léo Ducas, Eike Kiltz, Tancrède Lepoint, Vadim Lyubashevsky, John M. Schanck, Peter Schwabe, Gregor Seiler, and Damien Stehlé. CRYSTALS-Kyber Algorithm Specifications and Supporting Documentation (version 3.02). 2021. |
| [CRMRSSB23] | Eros Camacho-Ruiz, Macarena C. Martínez-Rodríguez, Santiago Sánchez-Solano, and Piedad Brox. Timing-attack-resistant acceleration of NTRU round 3 encryption on resource-constrained embedded systems. Cryptography, 7(2), 2023. |
| [DKL+21] | Léo Ducas, Eike Kiltz, Tancrède Lepoint, Vadim Lyubashevsky, Peter Schwabe, Gregor Seiler, and Damien Stehlé. CRYSTALS-Dilithium – Algorithm Specifications and Supporting Documentation (version 3.1). 2021. |
| [MRT15] | Somayya Madakam, R Ramaswamy, and Siddharth Tripathi. Internet of Things (IoT): A literature review. Journal of Computer and Communications, 3:164–173, 04 2015. |
| [PYN22] | PYNQ. PYNQ – Python Productivity for Zynq. http://www.pynq.io, 2022. Accessed: 2024-01-08. |
| [RPi23] | RPi4B. Raspberry Pi 4 model B specifications. https://www.raspberrypi.com/products/raspberry-pi-4-model-b/specifications/, 2023. Accessed: 2024-01-08. |


