Integrity Verification
Grazia D’Onghia and Antonio Lioy (Politecnico di Torino)
16/01/2025
Introduction
The advent of Cryptographically Relevant Quantum Computers (CRQCs) represents a paradigm shift in computing that threatens the foundational security of traditional asymmetric cryptographic systems such as RSA and ECC. These algorithms rely on mathematical problems that CRQCs could efficiently solve, as demonstrated by the Shor’s algorithm [1]. To address this imminent risk, there is an urgent need to transition to post-quantum cryptographic (PQC) algorithms that are designed to be resistant to both classical and quantum attacks [2], [3].
Integrity Verification techniques are vital for maintaining trust in modern computing environments. These mechanisms include secure boot, measured boot, and remote attestation. They are used to ensure and verify that systems operate only under the control of authorized code and with the expected configurations. In this way, they provide a strong defense against malicious code and unauthorized modifications. Remote attestation, in particular, enables systems to present verifiable integrity evidence to remote entities, a critical feature for distributed and cloud-based infrastructures.
Integrity verification heavily depends upon digital signatures, thus it is an area that requires quick evolution to PQC to avoid quantum-based attacks. The first essential step in this transition exercise is to evaluate the NIST PQC algorithms [4], in order to understand the most suitable ones for the specific use case. Since PQ digital signatures rely on different mathematical problems and use much larger keys than current signatures, we must evaluate compatibility with current instruction sets and network protocols.
The Commercial National Security Algorithm Suite 2.0 (CNSA2.0) [5] offers an important contribution from this point of view, as well as the ETSI White Paper [2], Cloudflare [6] and the BSI [7].
Our first contribution consists in combining the previous recommendations with our requirements to evaluate the best algorithms for Integrity Verification techniques within the QUBIP project.
The effort in the PQC transition relies in evaluating the overhead introduced by PQ algorithms (by means of memory consumption and speed) and choosing the best ones for constrained environments such as IoT devices. These new algorithms work with larger keys and signatures, thus leading to careful analysis of the trade-offs that should be made in order to have an improved security without a significant fall in performance.
PQ Software and firmware protection technologies
Modern software and firmware protection rely on three core techniques: secure boot, measured boot, and remote attestation. Here’s how these approaches can be adapted for quantum-safe security.
SECURE BOOT
Secure boot ensures that a device starts only with trusted software. This is achieved by verifying the signature created by the manufacturer over the boot components. Transitioning to a quantum-safe secure boot involves supporting a PQ signature in the boot sequence.
Key considerations include:
- PQC should be included at the firmware level, and the earlier it is included in the boot sequence, the better.
- PQ Digital Signatures should be used. They must offer long-term security. Hash-based schemes, such as SLH-DSA, XMSS, and LMS, are preferable due to their reliance on well-studied cryptographic hash functions, which are more mature than newer approaches like lattice-based schemes [8].
- Resource Constraints. On devices with limited memory, the size of keys, signatures, and auxiliary structures must be minimized.
- Minimizing implementation risks. Stateful algorithms like LMS or XMSS add complexity by requiring robust state management. Stateless options like SLH-DSA avoid this issue but come at a price, namely larger signatures and slower verification.
MEASURED BOOT
Measured boot establishes a chain of trust by cryptographically measuring each critical system component during boot, starting with the Core Root of Trust for Measurement (CRTM). The CRTM, implemented in immutable ROM, is a foundational element that can only transition to quantum-safe methods at the hardware level.
Each component is measured by the previous one (using secure hash functions) before gaining control of the platform.
Implementing a PQ measured boot requires adopting quantum-safe hash functions to generate cryptographic hashes of code and configurations.
While CRQC poses its biggest threat to classical asymmetric cryptographic algorithms, their impact on hash functions is less severe, but still significant.
For collision resistance, quantum computers do not provide a significant speedup over classical attacks; the best-known quantum attack does not significantly improve over the classical birthday attack, which halves the security strength [9].
To implement a quantum-safe measured boot, hash functions like SHA-384, SHA-512, or SHA-3-512 should be used, ensuring sufficient collision resistance against quantum threats, as Grover’s algorithm reduces classical hash strength [10].
The measurements acquired during the boot stages have to be recorded in a secure environment, which usually is the Trusted Platform Module (TPM) , either physical or firmware running inside a Trusted Execution Environment (TEE).
Afterwards, the recorded quantum-safe measurements will be available for use in the PQ Remote Attestation protocol.
REMOTE ATTESTATION
Remote Attestation (RA) verifies the integrity and trustworthiness of a remote system (the Attester) by having it provide a cryptographic proof of its state to a trusted party, the Verifier. In a challenge-response format, the Verifier sends a nonce (to avoid replay attacks), and the Attester replies with a signed evidence (called Quote) of its trustworthiness. The Quote contains the nonce and the measurements collected during the measured boot. This allows the Verifier to check if the system is trustworthy or it’s been tampered with.
In the case of PQ RA, the selected signature algorithm for the Quote should be computationally efficient, respectively for the signature generation at the Attester and verification at the Verifier. This impacts the attestation throughput: the faster the attestation process, the shorter the window of opportunity for attackers to exploit a compromised system.
Comparing the performance of the NIST PQ algorithms, FN-DSA represents an optimal choice for PQ RA because it provides the highest efficiency in signature generation and verification. However, it requires platforms to have a Floating Point Unit (FPU), which might be an issue. ML-DSA is also a suitable choice, having a good balance between signature generation, and verification efficiency, but it is slightly slower than FALCON. If the algorithm’s maturity is more important than the RA performance, SLH-DSA is the algorithm to use. It is evident that there is no clear winner, therefore enabling algorithm agility for RA signatures is desirable to support different use cases.
PQ Transition of Integrity Verification techniques within the QUBIP project
The objective within QUBIP is to perform the transition exercise of the aforementioned integrity verification techniques, in order to have secure and measured boot in IoT devices, and RA for both embedded systems and more powerful ones.
SECURE AND MEASURED BOOT IN EMBEDDED SYSTEMS
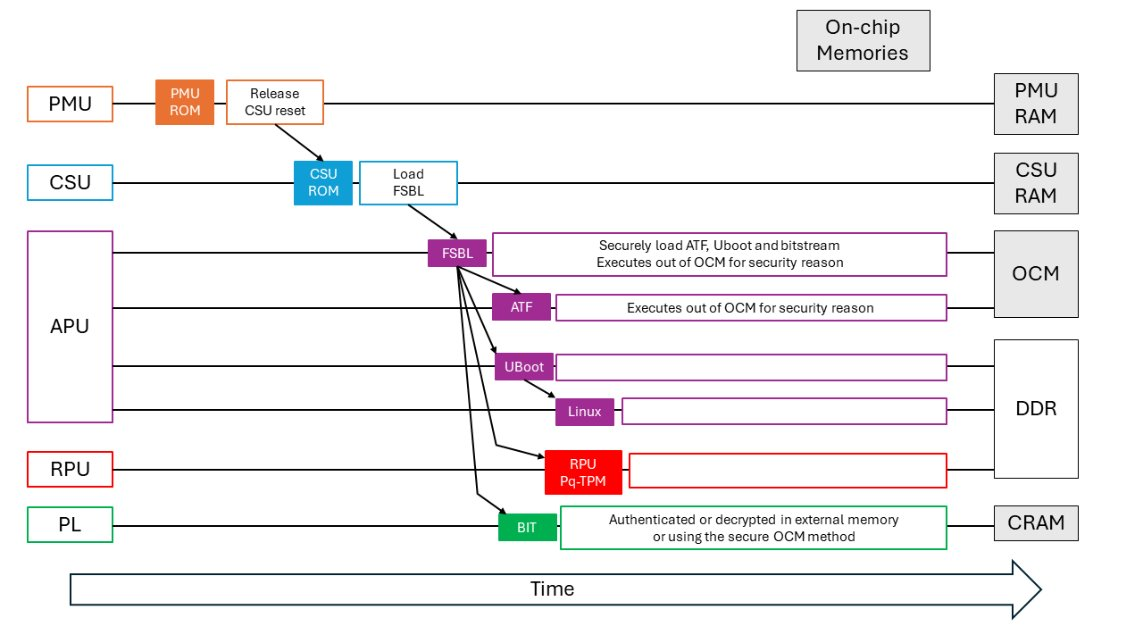
In order to integrate PQC in secure and measured boot, it is crucial to study the boot sequence of the target platform. QUBIP uses an ARM-based system. In its boot sequence, the earliest modifiable code is the First Stage Bootloader (FSBL), since all the previous partitions (CSU and PMU) are ROM-based. PQC can therefore be integrated in the FSBL, which authenticates and loads all the subsequent software components (Figure 1). Among them, there is the firmware TPM (fTPM) which runs inside a TEE and is in charge of storing the boot measurements and providing the quantum-safe signed quote for RA.
REMOTE ATTESTATION
Within QUBIP, RA is included in two flavours for the Attester, corresponding to two different platforms: ARM (for embedded systems) and x86 (for telco nodes). The latter implies the presence of a physical TPM, thus being different from the ARM one that uses a fTPM.
Since there is not yet a PQ TPM, the current efforts are focused on software modifications [11]. Therefore, the transition exercise for this use case would consist in performing a hybrid RA process, where both classical and PQ algorithms would be adopted.
Since a physical TPM can only perform classic digital signatures (such as RSA and ECDSA), the lowest level where PQC can be included through software is the Linux driver of the TPM. Therefore, the objective within QUBIP is to obtain a hybrid quote, signed with ECDSA by the physical TPM and then wrapped with a PQ signature at driver level.
Conclusion
QUBIP is making an exercise in addressing the practical challenges of integrating PQC into system integrity verification. By combining established cryptographic standards and emerging recommendations, the project provides a roadmap for adopting secure and measured boot, as well as remote attestation, using quantum-resistant algorithms.
Key considerations such as algorithm maturity, resource efficiency, and implementation compatibility remain central to achieve a smooth transition.
As we continue this exercise, the integration of PQC into foundational security technologies will play a decisive role in securing the digital landscape of the quantum era.


